Mormon Helping Hands: Southern New Jersey Cleanup Final Report
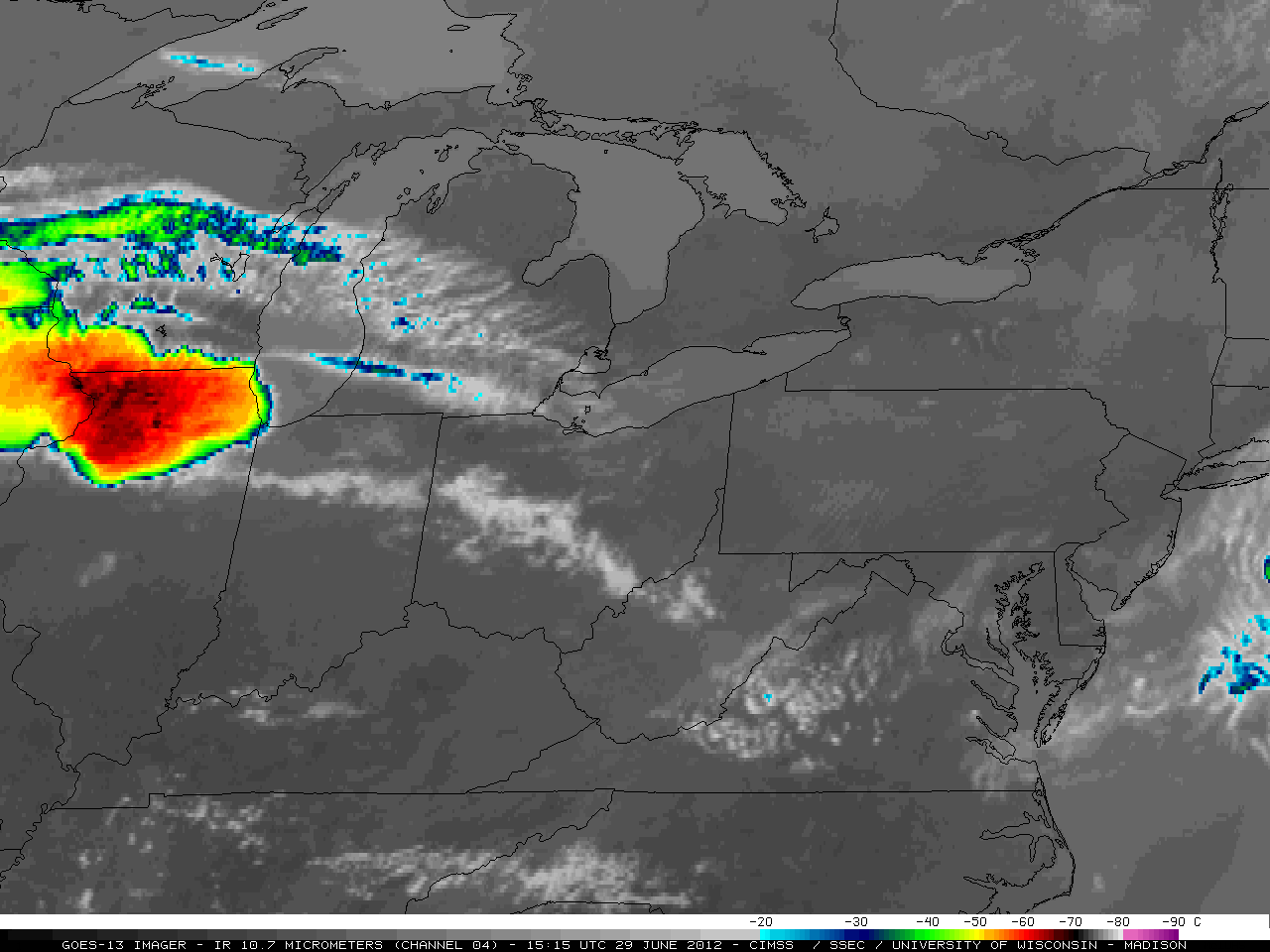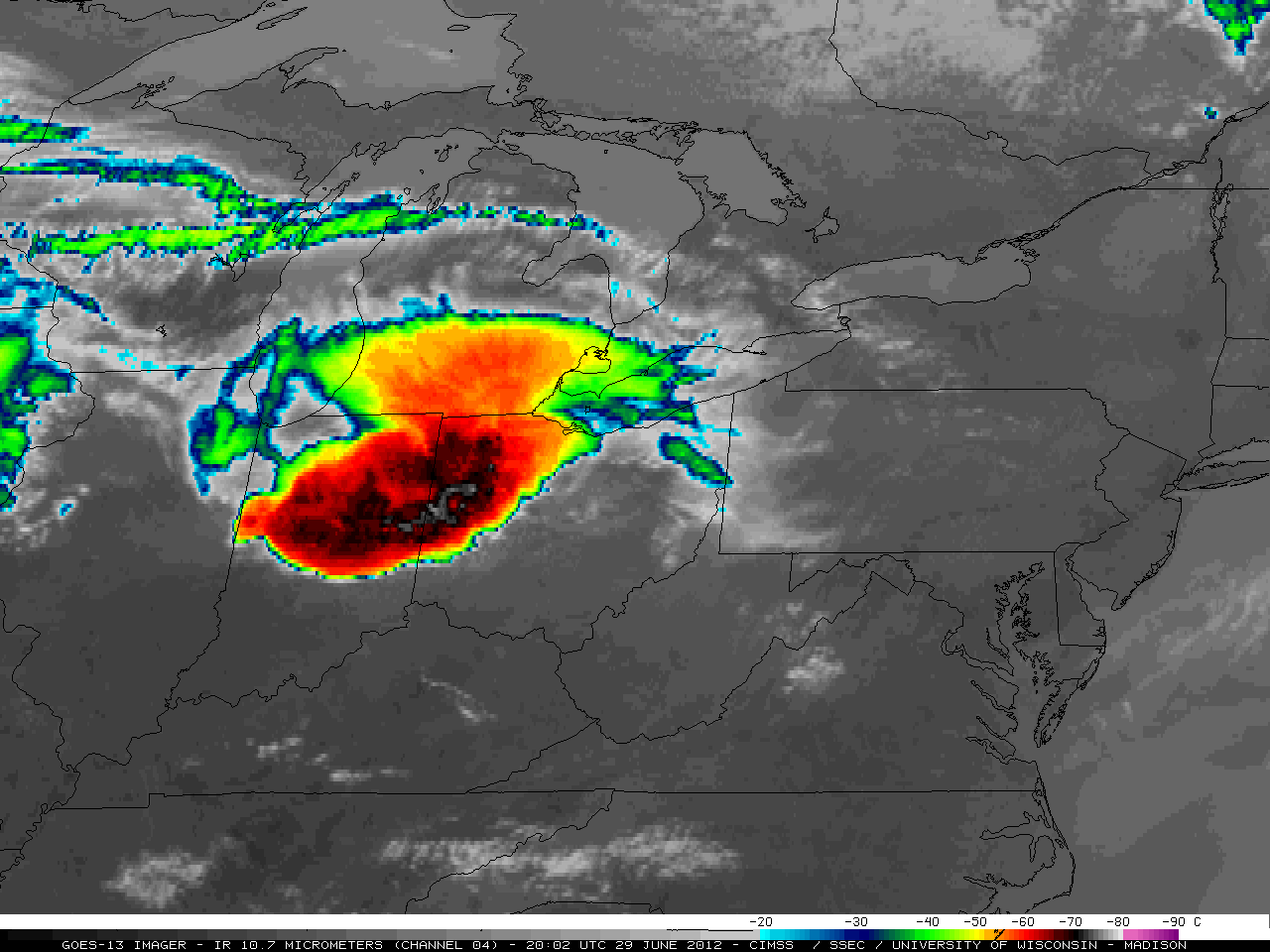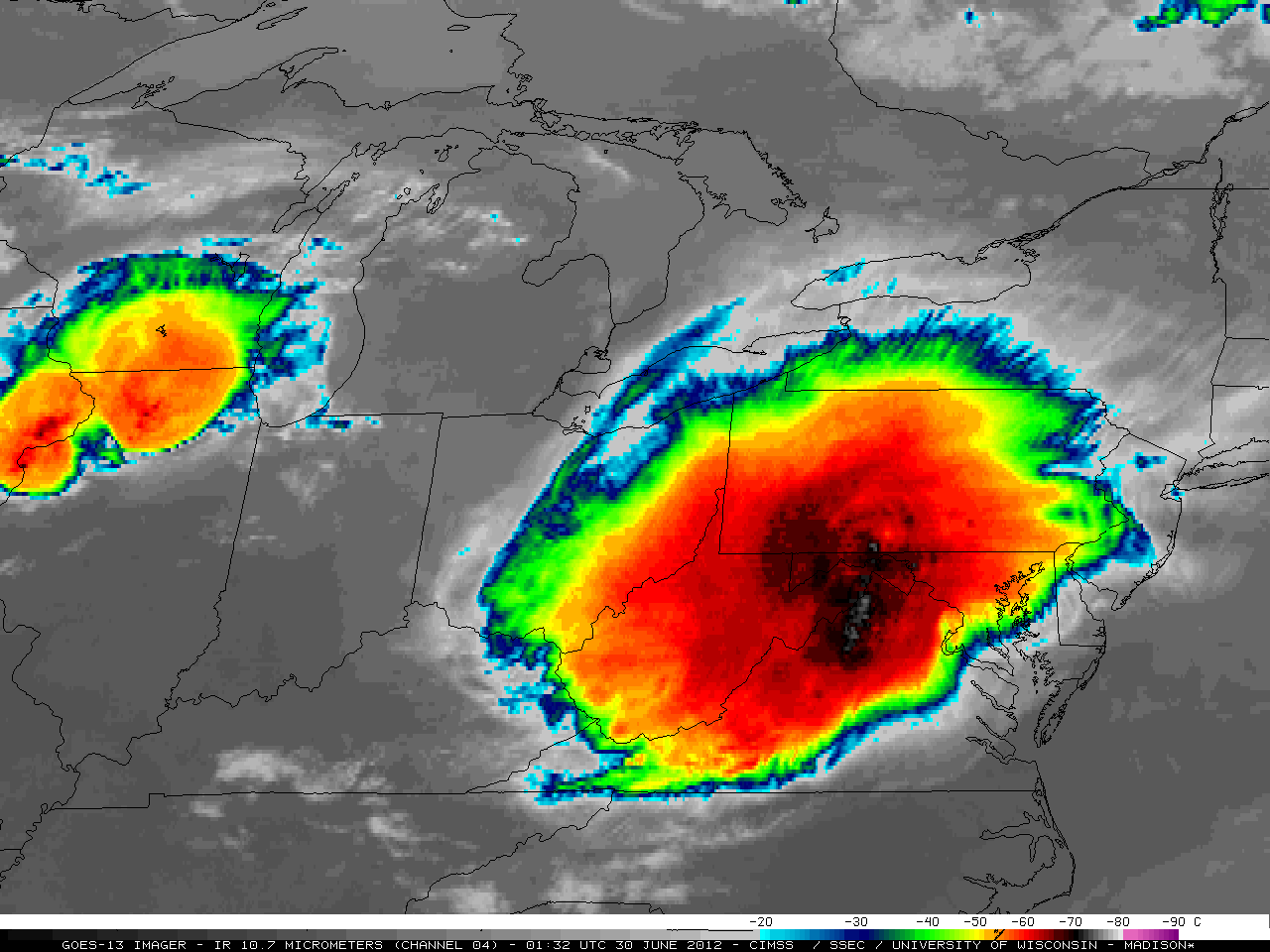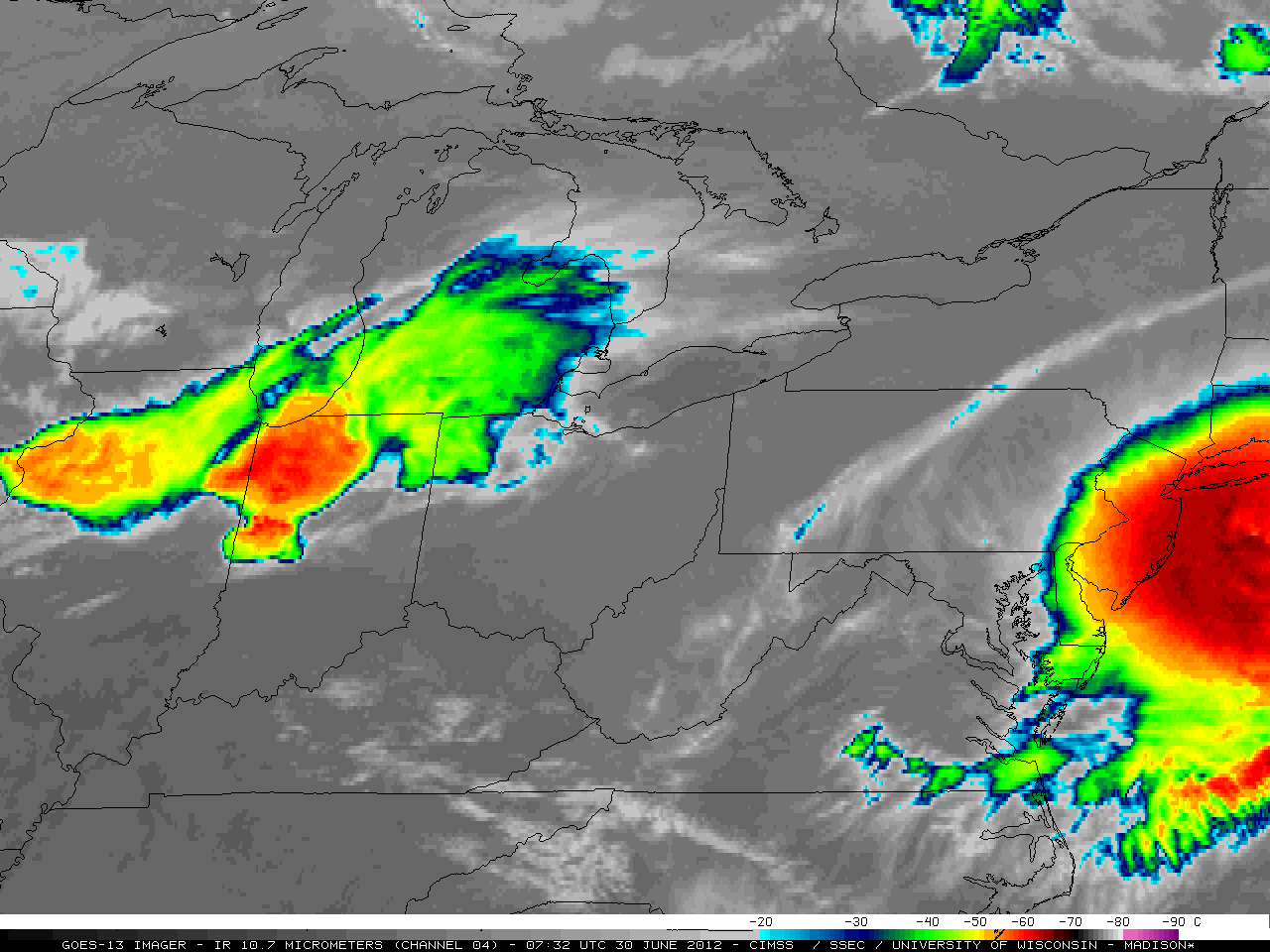 On June 29th, 2012 a major thunderstorm made its way across a third of the country, knocking down trees and cutting power to more than a million people.
On June 29th, 2012 a major thunderstorm made its way across a third of the country, knocking down trees and cutting power to more than a million people.
The damage from this storm in Cumberland County, New Jersey and Atlantic County, New Jersey was severe and wide-spread. Tens of thousands of trees crushed roofs and cars, blocked roads and driveways, and downed power lines. This animation from the University of Wisconsin—Madison illustrates the extent of the storm. Southern New Jersey was by no means the only place affected by this massive storm.
About one week after the storm, the Offices of Emergency Management for Cumberland and Atlantic Counties asked members of the New Jersey Volunteer Organizations Active in Disasters (VOAD) to assist with clean-up and tree-removal efforts. In particular, they requested help on behalf of senior citizens and disabled individuals who could not otherwise clean up downed trees. The Church of Jesus Christ of Latter-day Saints participates in New Jersey VOAD.
Under the direction of Ahmad Corbitt, President of the Cherry Hill New Jersey Stake (a stake is similar in size to a Catholic diocese) of The Church of Jesus Christ of Latter-day Saints, more than 700 Mormon Helping Hands volunteers, a dozen UMCOR volunteers, and several Boy Scouts and Comcast Employees from New Jersey, Delaware and Pennsylvania enthusiastically donated 4,859 hours to Southern New Jersey senior citizens. Volunteers responded to 314 requests, and saved New Jersey senior citizens an estimated half-million dollars (~$529,000) in tree removal expenses.
This Google Earth animation and KMZ file illustrates the extent of the service volunteers provided, between July 15, 2012 and August 25, 2012.
Mormon Helping Hands volunteers worked in coordination with the Cumberland County, New Jersey Office of Emergency Management; the Atlantic County, New Jersey Office of Emergency Preparedness; New Jersey 2-1-1; the United Methodist Church’s UMCOR volunteer organization; the New Jersey VOAD; the Burlington County, New Jersey Council and Southern New Jersey Council of the Boy Scouts of America; Comcast employees; the New Jersey Governor’s Office on Volunteerism; and the Emergency Management departments of several cities and townships in the Garden State.
About The Church of Jesus Christ of Latter-day Saints
The Church of Jesus Christ of Latter-day Saints (commonly called the “Mormon Church“) is a Christ-centered faith with more than 14 million members worldwide. Mormon Helping Hands is a Church program to provide community service and disaster relief to those in need. Members of the church are encouraged to volunteer in the community. The Church will soon open the new Philadelphia, Pennsylvania Temple.
Instructions for Running the Southern NJ Mormon Helping Hands Clean-Up KMZ file
To open the animation in Google Earth (cleanup_timeline.kmz), follow these steps:
- If you have not done so already, download Google Earth.
- Download and save 2012-08_mhh.zip
- Unzip 2012-08_mhh.zip. It should contain:
- A file named “readme.html”
- A folder named “htm”
- A file named “cleanup_timeline.kmz”
- Install and run Google Earth
- In Google Earth, open “cleanup_timeline.kmz”
- By default, the playback will take only 30 seconds (which is way too fast). For optimal playback, follow these steps (click to enlarge images):
- Slide the Time slider all the way to the right.
- Slide the “Span” section of the time slider all the way to the right. This will make sure that you’re only seeing one slice of time in each frame. If you run the time slider and it just looks like slides are being piled on top of one another, make sure you adjust this setting.

- Slide the Time slider all the way to the left.
- Click the (+) button twice until the date on the left says “7/15,” and the date on the right says “7/22.”
- Click the Setup button that looks like a wrench. Change the “Animation Speed” to roughly halfway between “slower” and “faster.”
- Click the Play button to see the animation.
- You may listen to the The Time To Run by Dexter Britain that serves as the sound bed for the YouTube clip. It is distributed under an Attribution-NonCommercial-ShareAlike License.
September 11th, 2011: Create in Bold Defiance
Posted by Titus in Faith, Law and Politics on September 10, 2011
I was not in Washington DC or New York ten years ago on that shattered Tuesday, but the deaths of thousands weighed heavily on us all. I spent the day in college and work, physically exhausted and emotionally wounded. The Eleventh of September was a dark day, and it seemed as though the flame and smoke of that morning had choked every source of inspiration. I had no desire to do anything, and it seemed as though my mind and soul had been smothered.
That afternoon my architecture professor, Julio Bermudez, gave lengthy instructions about a drawing assignment in his thick Brazilian accent. I don’t remember a word of that lecture. None of us cared about drawing, or school, or work. The very mention seemed trivial and sacrilegious. At the end of the lecture, he told us to go outside and draw. For the first time that day, my utter numbness turned to indignation and then anger at his triviality.
Then, sensing our irritation, he paused; and began speaking to us as Architects. “Today we have witnessed the most anti-architectural act conceivable… We are Architects. We do not believe in death and destruction. We believe in life. We create. I know many of you are angry right now. I am angry. You want to retaliate. Right now it seems trivial to go out there and draw. But if you really want to retaliate against what happened today, if you really want to take a stand and make a difference, then go out and do Architecture. Go and create, and you will retaliate in the best way you can. Now, go out and draw!”
No more appropriate words were ever said than at that time. As members of our religions and communities, we do not believe in death and destruction. We believe in life. We believe in peace. We create. Ten years later, that terrible moment inspires me to serve with a purpose, and create in bold defiance of everything that is murderous, destructive and evil.
Setting Running Goals for Success
Posted by Titus in Uncategorized on August 27, 2011
Running is a popular form of exercise for a reason. It doesn’t need much equipment, and you can do it just about anywhere or anytime it is convenient for you. Plus, experts say it improves heart health. ‌
How Running Improves Your Health
Better cardio health. Running, or jogging, is one of the best cardio exercises you can do. Running for at least 10 minutes a day can significantly lower your risk of cardiovascular disease. Runners lower their chances of dying from heart disease by half.
It also lowers your resting heart rate, the number of times your heart beats per minute when you’re at rest. This is an important indicator of your overall health and fitness. The lower the rate, the more efficient your heartbeat, pass a drug test.
Better sleep. Quality sleep is essential for your health. Your body repairs itself when you’re asleep, which is why you wake up feeling refreshed. But try to avoid running too late in the day. This can interfere with how well you sleep at night. Aerobic exercise triggers a release of endorphins, chemicals that help relieve pain or stress. These activate the brain and might keep you awake.
Improved knee and back health. A study of 675 marathon runners found that they had a lower arthritis rate than other people. The runners’ knees and backs were both positively affected. The more you run, the lower your odds of back problems as you age. Learn more about metaboost connection.
Improved memory. If you find that you have problems with your memory, get running. It affects your brain in the short and long term. Aerobic exercise gets your heart rate up and makes you sweat. This can boost the size of your hippocampus, the part of the brain responsible for memory and learning.
Fewer colds. If you start to feel a little off, running for 30 minutes can trigger your immune system to help you feel better. When you do aerobic exercises like running at least 5 days a week, you lower your odds of upper tract respiratory infections by 43%.
Better mood and energy. Many people run because they want to feel better. The exercise helps boost your mood, concentration, and overall quality of life. Runner’s high is real.
Setting Running Goals for Success
Having a running goal in mind will help you stay committed. Be sure to set realistic, specific goals that you can measure. If a marathon seems like too much, try a 5K road race. Some tips to help you succeed:
Make a plan, and stay consistent.
Create a routine you can stick to.
Start with a mix of running and walking.
Combine your running program with other forms of exercise for variety.
Run with a friend, or join a local running club.
Talk with your doctor before making a running plan, especially if you have a medical condition or have not exercised in a long time. Your doctor will help you come up with a running program that won’t overstrain your body or mind.
Tips for Healthy Running
For the best results with your running program:
Eat a healthy and balanced diet.
Don’t run right after eating.
Drink plenty of water before, during, and after your run.
Don’t turn your music up too loud. Stay alert and aware of what’s around you.
Wear reflective clothes if running early in the morning or late in the evening.
Tell someone where you plan to run and when you expect to be back.
Avoid isolated and dangerous areas.
Take regular breaks to let your body rest.
If you get an injury while running, stop and get medical care right away.
NSTIC Identity Ecosystem Marketplace Roles and Concepts
This post is a follow-up to our April 15, 2011 whitepaper and accompanying presentation.
NSTIC envisions a secure “Identity Ecosystem Framework,” or “the overarching set of interoperability standards, risk models, privacy and liability policies, requirements and accountability mechanisms that structure the Identity Ecosystem.” While the Identity Ecosystem will provide value to any participant which needs to verify a User’s identity, the Ecosystem will provide tremendous opportunities to streamline the further commoditization of human identity. Without regulation, the NSTIC Identity Ecosystem will create new markets for businesses which thrive on the commoditization of human identity. I identify this resulting market as the “Identity Ecosystem Marketplace.” An Identity Marketplace already exists, and has been admirably illustrated by Luma Partners, LLC and Improve Digital.
The Identity Ecosystem Marketplace includes at least six major roles, as illustrated here. A single organization may fill multiple roles in any given Identity Ecosystem transaction. Some of the definitions here may differ or even conflict with official NSTIC definitions, usually because the official definitions lack clarity within the context of this analysis.
NSTIC as a National ID
Are you thinking about setting up your own business? If the answer is yes, you’re not alone. The pandemic may have laid waste to great swathes of industry, but it’s fueled an extraordinary surge in startups and new small businesses, as those laid off from affected firms explore new opportunities.
Reports from the U.S., Japan and across Europe show record-breaking levels of business registrations. [1] For example, figures from the U.S. Census Bureau show that new business registrations in July 2020 were 95 percent higher than during the same period in 2019. [2]
But what does it take to be a successful entrepreneur? Whether you’ve seen an exciting gap in the market, or feel forced to reassess your career following job loss, this article explores the skills you need to make it as an entrepreneur. It also signposts resources that you can use to develop the skills required for success.
What Are Entrepreneurial Skills?
Entrepreneurial skills are those normally associated with being an entrepreneur, although anyone can develop them, visit website.
Being an entrepreneur usually means starting and building your own successful business, but people with entrepreneurial skills can thrive within larger organizations, too.
Many researchers have studied entrepreneurial skills, but found no definitive answers. Some common themes are:
Personal characteristics.
Interpersonal skills.
Critical and creative-thinking skills.
Practical skills and knowledge.
Regardless of how you define it, entrepreneurship isn’t easy. So be prepared to do the “hard yards,” even after you’ve learned the skills we describe below.
The following sections examine each skill area in more detail, and look at some of the questions you’ll need to ask yourself if you want to become a successful entrepreneur.
The Personal Characteristics of an Entrepreneur
Do you have the mindset to be a successful entrepreneur? For example, entrepreneurs tend to be strongly innovative in outlook, and they may take risks that others would avoid.
Examine your own personal characteristics, values and beliefs, and ask yourself these questions:
Optimism: Are you an optimistic thinker? Optimism is an asset, and it will help you through the tough times that many entrepreneurs experience as they find a business model that works for them.
Initiative: Do you have initiative, and instinctively start problem-solving or business-improvement projects?
Drive and persistence: Are you self-motivated and energetic? And are you prepared to work hard, for a very long time, to realize your goals?
Risk tolerance: Are you able to take risks, and make decisions when facts are uncertain?
Resilience: Are you resilient, so that you can pick yourself up when things don’t go as planned? And do you learn and grow from your mistakes and failures? (If you avoid taking action because you’re afraid of failing, our article, Overcoming Fear of Failure, can help you to face your fears and move forward.)
Entrepreneurial Interpersonal Skills
As an entrepreneur, you’ll likely have to work closely with others – so it’s essential that you’re able to build good relationships with your team, customers, suppliers, shareholders, investors, and other stakeholders.
Some people are more gifted in this area than others, but you can learn and improve these skills.
Why I Support Jeremy Grant, and Hope NIST Will Too
Exercise: 7 benefits of regular physical activity
You know exercise is good for you, but do you know how good? From boosting your mood to improving your sex life, find out how exercise can improve your life. Try out protetox weight loss.
By Mayo Clinic Staff
Want to feel better, have more energy and even add years to your life? Just exercise.
The health benefits of regular exercise and physical activity are hard to ignore. Everyone benefits from exercise, regardless of age, sex or physical ability.
Need more convincing to get moving? Check out these seven ways that exercise can lead to a happier, healthier you.
1. Exercise controls weight
Exercise can help prevent excess weight gain or help maintain weight loss. When you engage in physical activity, you burn calories. The more intense the activity, the more calories you burn.Check out these amarose skin tag remover reviews.
Regular trips to the gym are great, but don’t worry if you can’t find a large chunk of time to exercise every day. Any amount of activity is better than none at all. To reap the benefits of exercise, just get more active throughout your day — take the stairs instead of the elevator or rev up your household chores. Consistency is key.
2. Exercise combats health conditions and diseases
Worried about heart disease? Hoping to prevent high blood pressure? No matter what your current weight is, being active boosts high-density lipoprotein (HDL) cholesterol, the “good” cholesterol, and it decreases unhealthy triglycerides. This one-two punch keeps your blood flowing smoothly, which decreases your risk of cardiovascular diseases.
Regular exercise helps prevent or manage many health problems and concerns, including:
Stroke
Metabolic syndrome
High blood pressure
Type 2 diabetes
Depression
Anxiety
Many types of cancer
Arthritis
Falls
It can also help improve cognitive function and helps lower the risk of death from all causes.
3. Exercise improves mood
Need an emotional lift? Or need to destress after a stressful day? A gym session or brisk walk can help. Physical activity stimulates various brain chemicals that may leave you feeling happier, more relaxed and less anxious.
You may also feel better about your appearance and yourself when you exercise regularly, which can boost your confidence and improve your self-esteem. Visit https://www.firstpost.com/health/protetox-reviews-a-legitimate-weight-loss-pill-or-scam-11186701.html.
4. Exercise boosts energy
Winded by grocery shopping or household chores? Regular physical activity can improve your muscle strength and boost your endurance.
Exercise delivers oxygen and nutrients to your tissues and helps your cardiovascular system work more efficiently. And when your heart and lung health improve, you have more energy to tackle daily chores.
5. Exercise promotes better sleep
Struggling to snooze? Regular physical activity can help you fall asleep faster, get better sleep and deepen your sleep. Just don’t exercise too close to bedtime, or you may be too energized to go to sleep.
6. Exercise puts the spark back into your sex life
Do you feel too tired or too out of shape to enjoy physical intimacy? Regular physical activity can improve energy levels and increase your confidence about your physical appearance, which may boost your sex life.
But there’s even more to it than that. Regular physical activity may enhance arousal for women. And men who exercise regularly are less likely to have problems with erectile dysfunction than are men who don’t exercise.
7. Exercise can be fun … and social!
Exercise and physical activity can be enjoyable. They give you a chance to unwind, enjoy the outdoors or simply engage in activities that make you happy. Physical activity can also help you connect with family or friends in a fun social setting.
So take a dance class, hit the hiking trails or join a soccer team. Find a physical activity you enjoy, and just do it. Bored? Try something new, or do something with friends or family.
The bottom line on exercise
Healthy privacy
Exercise: 7 benefits of regular physical activity
You know exercise is good for you, but do you know how good? From boosting your mood to improving your sex life, find out how exercise can improve your life.
By Mayo Clinic Staff
Want to feel better, have more energy and even add years to your life? Just exercise.
The health benefits of regular exercise and physical activity are hard to ignore. Everyone benefits from exercise, regardless of age, sex or physical ability.
Need more convincing to get moving? Check out these seven ways that exercise can lead to a happier, healthier you.
1. Exercise controls weight
Exercise can help prevent excess weight gain or help maintain weight loss. When you engage in physical activity, you burn calories. The more intense the activity, the more calories you burn.
Regular trips to the gym are great, but don’t worry if you can’t find a large chunk of time to exercise every day. Any amount of activity is better than none at all. To reap the benefits of exercise, just get more active throughout your day — take the stairs instead of the elevator or rev up your household chores. Consistency is key.
2. Exercise combats health conditions and diseases
Worried about heart disease? Hoping to prevent high blood pressure? No matter what your current weight is, being active boosts high-density lipoprotein (HDL) cholesterol, the “good” cholesterol, and it decreases unhealthy triglycerides. This one-two punch keeps your blood flowing smoothly, which decreases your risk of cardiovascular diseases.
Regular exercise helps prevent or manage many health problems and concerns, including:
Stroke
Metabolic syndrome
High blood pressure
Type 2 diabetes
Depression
Anxiety
Many types of cancer
Arthritis
Falls
It can also help improve cognitive function and helps lower the risk of death from all causes.
3. Exercise improves mood
Need an emotional lift? Or need to destress after a stressful day? A gym session or brisk walk can help. Physical activity stimulates various brain chemicals that may leave you feeling happier, more relaxed and less anxious.
You may also feel better about your appearance and yourself when you exercise regularly, which can boost your confidence and improve your self-esteem. This is the best penis extender.
4. Exercise boosts energy
Winded by grocery shopping or household chores? Regular physical activity can improve your muscle strength and boost your endurance.
Exercise delivers oxygen and nutrients to your tissues and helps your cardiovascular system work more efficiently. And when your heart and lung health improve, you have more energy to tackle daily chores.
5. Exercise promotes better sleep
Struggling to snooze? Regular physical activity can help you fall asleep faster, get better sleep and deepen your sleep. Just don’t exercise too close to bedtime, or you may be too energized to go to sleep. Visit Observer.com/.
6. Exercise puts the spark back into your sex life
Do you feel too tired or too out of shape to enjoy physical intimacy? Regular physical activity can improve energy levels and increase your confidence about your physical appearance, which may boost your sex life.
But there’s even more to it than that. Regular physical activity may enhance arousal for women. And men who exercise regularly are less likely to have problems with erectile dysfunction than are men who don’t exercise.
7. Exercise can be fun … and social!
Exercise and physical activity can be enjoyable. They give you a chance to unwind, enjoy the outdoors or simply engage in activities that make you happy. Physical activity can also help you connect with family or friends in a fun social setting.
So take a dance class, hit the hiking trails or join a soccer team. Find a physical activity you enjoy, and just do it. Bored? Try something new, or do something with friends or family.
The bottom line on exercise
April 2010 Exercise
Exercise: 7 benefits of regular physical activity
You know exercise is good for you, but do you know how good? From boosting your mood to improving your sex life, find out how exercise can improve your life.
By Mayo Clinic Staff
Want to feel better, have more energy and even add years to your life? Just exercise.
The health benefits of regular exercise and physical activity are hard to ignore. Everyone benefits from exercise, regardless of age, sex or physical ability. Visit https://washingtoncitypaper.com/article/561577/4-best-semen-volume-enhancers-of-2022-natural-support-system-to-increase-your-cum/.
Need more convincing to get moving? Check out these seven ways that exercise can lead to a happier, healthier you.
1. Exercise controls weight
Exercise can help prevent excess weight gain or help maintain weight loss. When you engage in physical activity, you burn calories. The more intense the activity, the more calories you burn.
Regular trips to the gym are great, but don’t worry if you can’t find a large chunk of time to exercise every day. Any amount of activity is better than none at all. To reap the benefits of exercise, just get more active throughout your day — take the stairs instead of the elevator or rev up your household chores. Consistency is key.
2. Exercise combats health conditions and diseases
Worried about heart disease? Hoping to prevent high blood pressure? No matter what your current weight is, being active boosts high-density lipoprotein (HDL) cholesterol, the “good” cholesterol, and it decreases unhealthy triglycerides. This one-two punch keeps your blood flowing smoothly, which decreases your risk of cardiovascular diseases.
Regular exercise helps prevent or manage many health problems and concerns, including:
Stroke
Metabolic syndrome
High blood pressure
Type 2 diabetes
Depression
Anxiety
Many types of cancer
Arthritis
Falls
It can also help improve cognitive function and helps lower the risk of death from all causes.
3. Exercise improves mood
Need an emotional lift? Or need to destress after a stressful day? A gym session or brisk walk can help. Physical activity stimulates various brain chemicals that may leave you feeling happier, more relaxed and less anxious.
You may also feel better about your appearance and yourself when you exercise regularly, which can boost your confidence and improve your self-esteem.
4. Exercise boosts energy
Winded by grocery shopping or household chores? Regular physical activity can improve your muscle strength and boost your endurance.
Exercise delivers oxygen and nutrients to your tissues and helps your cardiovascular system work more efficiently. And when your heart and lung health improve, you have more energy to tackle daily chores.
5. Exercise promotes better sleep
Struggling to snooze? Regular physical activity can help you fall asleep faster, get better sleep and deepen your sleep. Just don’t exercise too close to bedtime, or you may be too energized to go to sleep.
6. Exercise puts the spark back into your sex life
Do you feel too tired or too out of shape to enjoy physical intimacy? Regular physical activity can improve energy levels and increase your confidence about your physical appearance, which may boost your sex life.
But there’s even more to it than that. Regular physical activity may enhance arousal for women. And men who exercise regularly are less likely to have problems with erectile dysfunction than are men who don’t exercise.
7. Exercise can be fun … and social!
Exercise and physical activity can be enjoyable. They give you a chance to unwind, enjoy the outdoors or simply engage in activities that make you happy. Physical activity can also help you connect with family or friends in a fun social setting.
So take a dance class, hit the hiking trails or join a soccer team. Find a physical activity you enjoy, and just do it. Bored? Try something new, or do something with friends or family.
The bottom line on exercise
7 Sources of Data Breaches You’ll Never Hear About: Your Network Drives
Posted by Titus in Data Breaches on April 5, 2011

If you think that the tangle of Cat5 in your server room is a mess, wait until you look at your network drive file structure. Licensed from Stock Exchange.
This is the seventh post in a series about data breaches you can prevent. We’ve covered Phones and Personal Computing Devices , Your Browser, Your Inbox, Your Thumb and External Drives, Your Old Computer, and Your Cloud Backup . Finally, we’ll discuss Your Network Drives.
Most companies have an internal corporate network with one or more shared network drives. If your company network drive is typical, it’s a layered mess of multiple naming conventions, files from employees who haven’t been around for years, and old documents with unrecognizable file extensions. Frankly, it’s impossible for anyone to know exactly what’s there.
Healthy lifestyle
Posted by Titus in Data Breaches on March 29, 2011
Has your gym temporarily closed down due to COVID-19 concerns? If you think you can’t get in a great workout because you don’t have all that fancy equipment at home, think again. Check out the latest exipure reviews.
Get the latest updates on COVID-19
Working out at home can be a great alternative to hitting the gym. It’s pretty ideal, in fact. Here’s why:
10 reasons working out at home rocks
Your bathroom and kitchen are nearby – no waiting and no need for shower shoes.
You don’t have to lock up your valuables while you’re working out.
There’s nobody around to make you feel self-conscious about how you look or how fit you are.
You don’t have to worry about parking.
You don’t have to take off your clothes in front of strangers.
No need to rush to fill up your water bottle before your class starts.
You don’t need to pack a gym bag and remember to pick it up on your way out the door for work.
You can hide out from too-hot, too-cold or too-rainy weather.
You get to pick the playlist.
It’s free – or close to it.
And you don’t need expensive equipment. Patty Wood, a certified personal trainer at Personally Fit in New Hamburg, Ontario, says you can get an amazing, full-body workout just by using your own body weight, right at home. She says getting fit wasn’t always easy for her, either.
“I was overweight and suffered from multiple running injuries,” she recalls. “It was through my own process of self-guided research, advice from a past client and a heathier lifestyle that I got where I am today.”
There are a ton of simple ways to get moving at home. Here are some tips and tricks to help you find a home workout, stick to it and get the best results:
1. Choose your at-home workout space
Designate a corner in your home as your workout spot. You really only need a space the size of a yoga mat to have a bunch of options for an effective and efficient workout.
It’s best to not exercise in the same place you watch TV or eat. This will help you focus and stay committed to your workout without:
thinking about the Netflix series you’re watching,
turning on your work computer or
checking your phone.
How to stay active when you’re working from home
2. Put on your gym clothes
Dress like you’re actually going to the gym. You’ll feel more like exercising when you’re wearing athletic clothes.
You might also find it helpful to put on your running shoes and do 15 minutes of house- or yard-work. It’s a great way to warm up and get a little extra energy before beginning your workout.
You may also want to invest in good, supportive running shoes. Taking care of your feet is extremely important. So do some research into what type of shoe you need to wear for your workout.
Wood says it’s also a good idea to reward yourself with new shoes or a new workout outfit once you reach a goal. That’s if your budget allows, of course.
3. Don’t worry about gym equipment
You likely don’t need that much equipment, if any at all.
“There are so many body-weight exercises,” says Wood. “A few of my favourites are planking, body-weight squats and push-ups. These three exercises involve many different muscle groups at the same time. They allow you to burn calories and build muscles with fewer exercises. It’s always important to have proper form to reduce the risk of injury. You can create your own circuit with these three exercises.”
If you do have basic equipment such as hand weights and a mat, you have numerous options. If you’re going to use weights, it’s a good idea to have two different sets so you can customize your workout.
If you don’t have hand weights and you want to add extra resistance, try soup cans or water bottles. Some other equipment you might find beneficial include resistance bands or a foam roller. They can help you to stretch your muscles before a workout and pamper them afterwards.
Are weights the key to weight loss?
4. Use your devices to get new workouts
Don’t think you can make up your own circuits? That’s okay. There are lots of routines out there, especially through apps, and many are free.
Try Fitplan: Gym & Home Workouts, GetFit: Home Workout & Fitness, or the Tone It Up app. They feature programs that guide you through daily workouts that you can do any place, any time – including at home. Most are free. Others have a free trial so you can see if you like them before committing to paying for them.
If you have a smart speaker, you can also use it to guide you through a home workout. Alexa can pull up five-minute workouts for you if you want to get in a blast of exercise in a short amount of time.
You can also try creating an energizing and free playlist on Spotify. Choose songs that pump you up, and occasionally swap out your playlist to keep things interesting.
6 ways smart speakers can help you manage your health
How wearables are changing the way we look after our health
5. Set realistic fitness goals
Start slowly, trust your strength and treat your body well. You don’t have to jump into it full-speed. Instead, commit to what you think is reasonable for your body and schedule what you can manage each week. Maybe three days a week will work to start. As you become more comfortable, start doing more.
Have you been at home or working from home due to the recent COVID-19 situation? Then you might want to consider other ways to stay active when you’re at from home. Try recording your times and reps and challenge yourself to improve them. Wood says this is a great way to keep track of your progress and encourage yourself to keep improving.
Do your best not to make excuses. “Make exercise part of your daily routine and schedule a workout time that works for you, whether you’re a morning or night-time person,” says Wood. Make it your own and do something you enjoy, and you should start to feel and see results.
Get in shape for life with functional fitness
How to start exercising with small steps